Recently, several of our RIA clients have received suspicious emails claiming to be from FINRA. The suspicious emails used the subject line “New FINRA Request – (Firm Name),” and came from an email address with the domain, “@gateway-finra.org” Below is a screenshot of one of these suspicious emails.
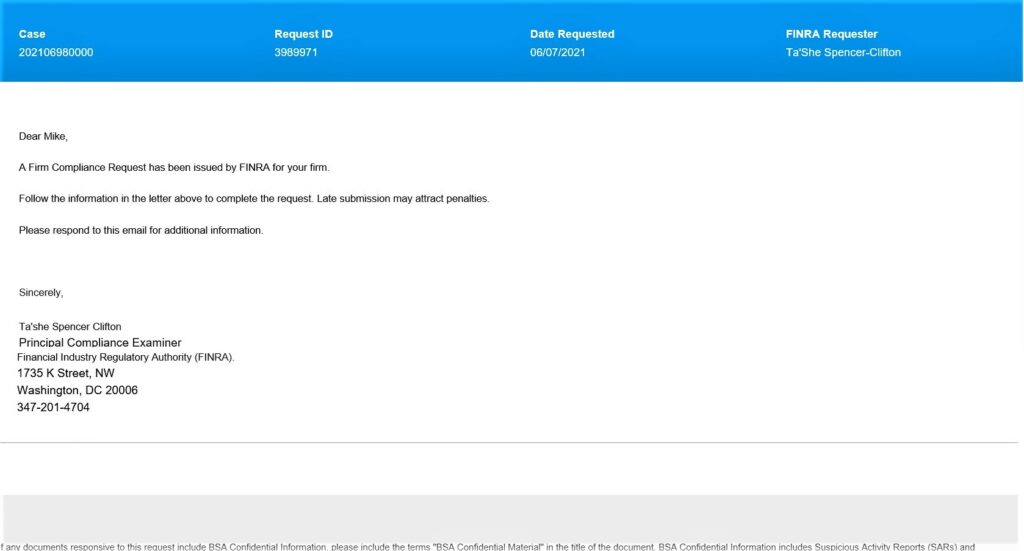
If you received a similar email do not click any links in the email or call the contact phone number. These emails are a part of a phishing attack. If you received one of these emails, delete it and notify all employees and personnel that such emails are circulating and instruct staff not to click any links and to delete such emails.
RIA Compliance Consultants reached out to FINRA which notified us that they are aware of the phishing email and have taken steps to address it and shut it down. FINRA explained that anyone who received such an email should block the domain. FINRA will never send an email coming from @gateway-finra.org and will only send an email from @finra.org.
In the event that a member of your staff does click a link that is part of a phishing attack, RIA Compliance Consultants recommends that you discuss the following best practices with information security staff and consultants.
- Activate Incident Response Plan.
- Retain Cybersecurity Expert.
- Interview Clicker(s). You and your cybersecurity expert should ask any and all clickers what happened, what they saw and if anything strange or out of place occurred after interacting with the phish.
- Obtain Copy of Email. Your cybersecurity expert should obtain the phishing email with full headers showing routing info especially the IP routing address that the phishing message came from (which will be a compromised machine).
- Mine Web for Threat Intelligence. Your cybersecurity expert will take the URLs and attachments to a sandbox and lookup sites. You should not go to the malicious site – do not paste the URL in your browser.
- Search Internal Systems. Your cybersecurity expert will need to check firewall logs to see if there was any traffic leaving your network to suspicious IPs or URLs. Additionally, your cybersecurity expert will need to search DNS logs and DHCP logs. Keep copies of logs.
- Check for Active Sessions. Your cybersecurity expert should check to make sure that the affected users don’t have active sessions. Look for VPNs and Citrix connections and whether they should be active.
- Review Mail Server Logs. Your cybersecurity expert should check to see which users received the message by searching your mail server logs. Search on message ID, source IPs, From, Subject and file attachment name.
- Adjust Email Filters. In order to avoid other users from falling victim to same attack, look for attributes in the email that you can filter for the firm’s email accounts.
- Change Passwords. If your investment adviser firm’s supervised persons or clients clicked the wrong link or provided information in response to a phishing scam, the passwords of the applicable individual(s) should be changed immediately on all of the individual’s accounts. The individual should create unique, non-dictionary, complicated, long (15 characters) passwords.
- Unique Passwords. Require use of unique password- especially do not permit use of same password throughout systems.
- Long Passwords. Require the unique password to be a non-dictionary alpha-numeric password of at least 15 characters/digits long (the longer, the better). A weak password isn’t acceptable even if you utilize two-factor authentication.
- Problematic Password Practices. Avoid using word “password” or derivative such as “passw@rd” in the password. Do not use birthdates, addresses or family member names in passwords. Refrain from using one simple word password like “monkey” or “football” for example. Do not place special characters (e.g., @, #, $) only at beginning or end of password. Password should not include common patterns.
- Password Re-set. Require re-set of password after 120 days. If system doesn’t allow for automatic re-set, set calendar reminders. Although not advisable to use a public computer, if a public computer is used and a password is entered, then the password should be re-set immediately from secure device or computer.
- Password Encryption. Require use of encrypted password manager/database. (Some experts are concerned about encrypted password manager being hacked.)
- Two-Factor Authentication to Access Email from New Device. Turn-on two-factor authentication to access email account from a new device or outside of the network. Certain security experts believe its preferable/safer to receive 2nd factor by special authenticator app (e.g., Google Authenticator, Authy, Microsoft Authenticator) rather than by text due to risk of a mobile phone’s SIM becoming compromised or the text message being intercepted. Check Regularly Accounts. Client should review client’s brokerage, investment advisory, bank and credit card accounts regularly to be sure no suspicious activity is taking place. You may also opt to leave the fraud alert on your credit report for a while until you’re absolutely certain you’re out of the proverbial hot water.
The above list of actions is by no means an exhaustive one. It is merely a starting point. You should seek advice from a cybersecurity expert on how to respond to becoming a victim of a phishing attack.
Resources
The following resources are best practices that an investment adviser should discuss with its information security staff and consultants.
How to Avoid Phishing Scams Employee Training
Cybersecurity Best Practices Checklist
Cybersecurity – Best Practices for Avoiding and Responding to Phishing Attacks
Cybersecurity – Phishing Email – Letter Notifying Client
Disclosure: RIA Compliance Consultants is not an expert in information security. Our employees are not trained or certified in information security. We do not provide information security risk assessments or audits of information security plans. RIA Compliance Consultants offers the above best practices and techniques for the reader to start a discussion with his or her IT & information security staff or consultants.
Posted by RCC
Labels: Cyber Security, Cybersecurity, Uncategorized
Tagged: Phishing